Web Application Firewall (WAF) Vs. Network Firewall: The Ultimate Manual
Cyberattacks are seemingly getting more sophisticated by the day. And organizations are using more applications, collecting more data, and relying on complex network infrastructures more than ever before.
It can be disastrous for your business if you’re not taking the right steps to secure your network traffic and business apps.
As you’re looking for the best ways to harden digital security, you’re likely finding two main options to stop attacks—web application firewalls (WAFs) and network firewalls.
Which one is the best option for your organization? The answer might surprise you.
Continue below to decide whether a WAF or network firewall is right for your business.
Our Recommendation = Get Both
The vast majority of modern enterprises need web application firewalls and network firewalls. There are some use-case-specific instances where you might need one and not the other, but we’ll cover those rare scenarios later on.
So why both?
Being forced to choose between a WAF and a network firewall is like a city mayor having to choose between a police department or a fire department. Each one stops a different type of threat. Choosing one over the other still leaves your organization vulnerable to specific attacks.
Historically, businesses relied on network firewalls to protect data and users. But network firewalls lack the ability to protect against modern security threats, especially for businesses using SaaS solutions, public clouds, and employing bring-your-own-device (BYOD) policies. That’s where WAFs come into play.
What’s the difference between a web application firewall and a network firewall?
Network firewalls protect unauthorized access to private networks. This is accomplished by defining specific policies for authorized access and blocking all other attempts by default.
WAFs specifically protect application traffic. It secures HTTP and HTTPS traffic and applications within the web-facing zones of your company network. WAFs prevent attacks like cross-site scripting (XSS), SQL injections, and distributed denial of service (DDoS) at the application level.
Most organizations need both of these firewalls to properly secure networks and applications. A network firewall alone won’t prevent certain web-based attacks on application traffic, and WAF alone won’t be enough to secure other parts of your network from unauthorized traffic. The two types of firewalls complement each other to offer complete security at multiple levels.
Firewall providers have recently come up with new technology, branded as “NGFW”—next-generation firewalls. Many NGFWs combine the capabilities of WAFs and network firewalls into a single solution. Fortinet is one example of an industry leader in this space paving the way with NGFWs.
But even with next-gen technology, most organizations will still need a dedicated WAF in conjunction with a network firewall or NGFW.
Refer back to the analogy we discussed earlier with police officers and firefighters. You could equip cop cars with fire extinguishers, but you can’t turn a police cruiser into a fire engine and still keep it functional for high-speed chases. The same concept can be applied to NGFWs and WAFs—they both provide valuable security services, but they’re not interchangeable.
Let’s take a look at situations when you might need one of these security technologies but not the other.
When to Get a Web Application Firewall (WAF)
As the name implies, web application firewalls are a bigger priority to any user or stakeholder serving the app. This includes application developers.
The person who writes the code of an application will have a deeper understanding of how to protect it. So they can create a web application firewall policy that addresses any weak points or vulnerabilities within the application.
WAFs are still part of infrastructure security, but developer collaboration is crucial when you’re integrating WAFs into the development process.
You can always get a basic WAF if you’re just running a website and want to protect it from SQL injections, XSS, and other web-based attacks. In this scenario, a network firewall may not be necessary.
When to Get a Network Firewall
Traditional firewalls are used to protect individual users and a network of individuals within an organizational network. They’re designed for local area networks (LAN) and IT networks.
Network firewalls defend against unauthorized network access, privileged escalations, DDoS attacks at the network level, and man-in-the-middle attacks.
They’re also better for organizations running on a non-hybrid network. If you’re not relying on SaaS, hybrid clouds, and your staff is only using local devices on the network, then a traditional network firewall should be suitable for your needs.
This is rarely the case with modern enterprises. But some smaller companies could fall into this category.
If you’re going to get a network firewall on its own, it’s definitely in your best interest to get an NGFW.
While this won’t necessarily provide all the benefits of a WAF, you’ll still have increased security and more flexibility with what you can accomplish compared to legacy firewalls.
Pricing – Is a Web Application Firewall or Network Firewall the Better Deal?
Getting a good deal on your WAF and network firewall is reliant on several factors. It’s unfair to say that one is a better deal than the other, as the cost varies based on the provider, hardware, technology, and network complexity.
For example, let’s stick with traditional network firewalls for a moment. Cisco, an industry leader in this space, has nine different categories for you to choose from.
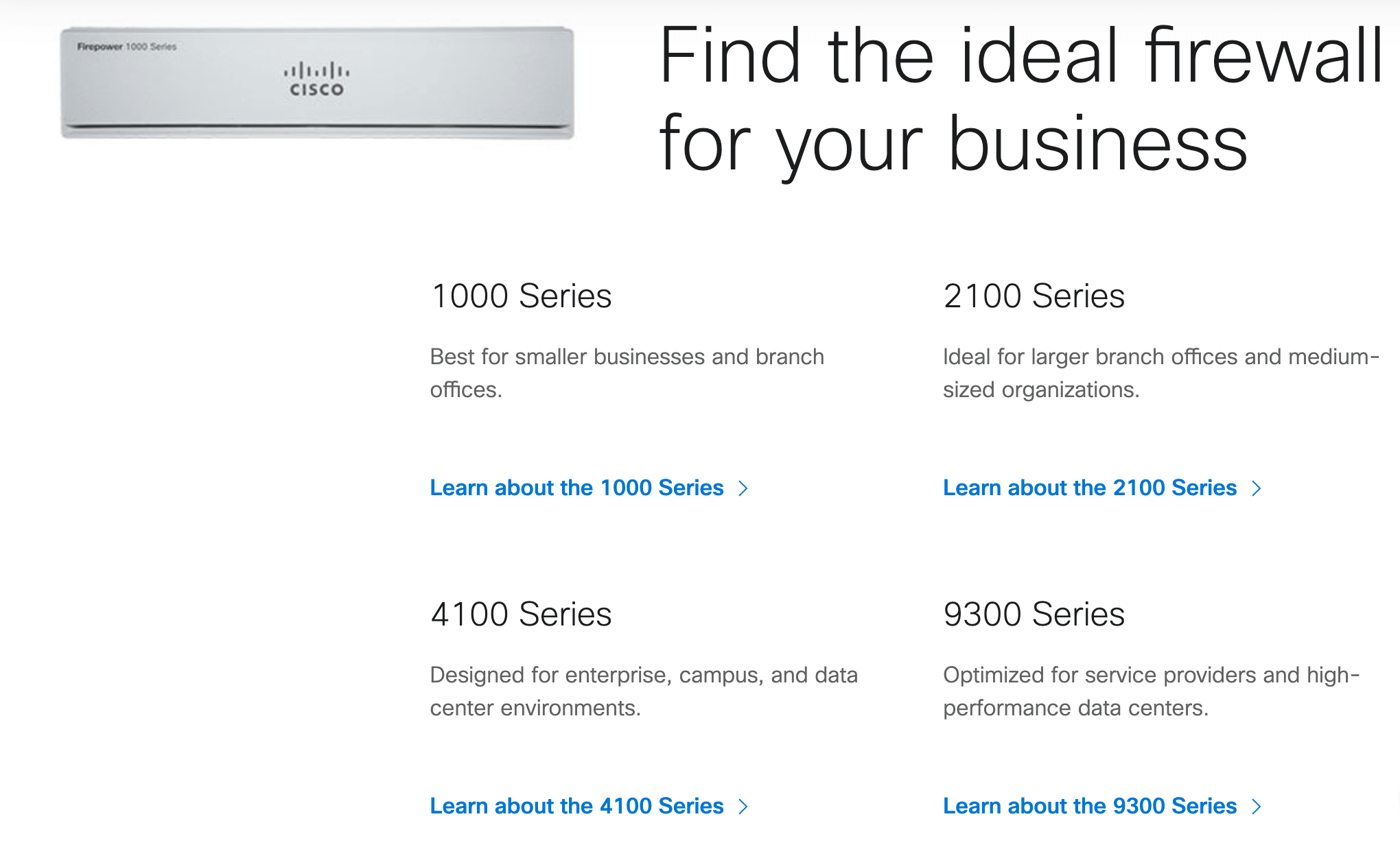
Within each category, you’ll find different firewall models and specifications for each.
Here’s a closer look at the Cisco 1000 firewall series models:
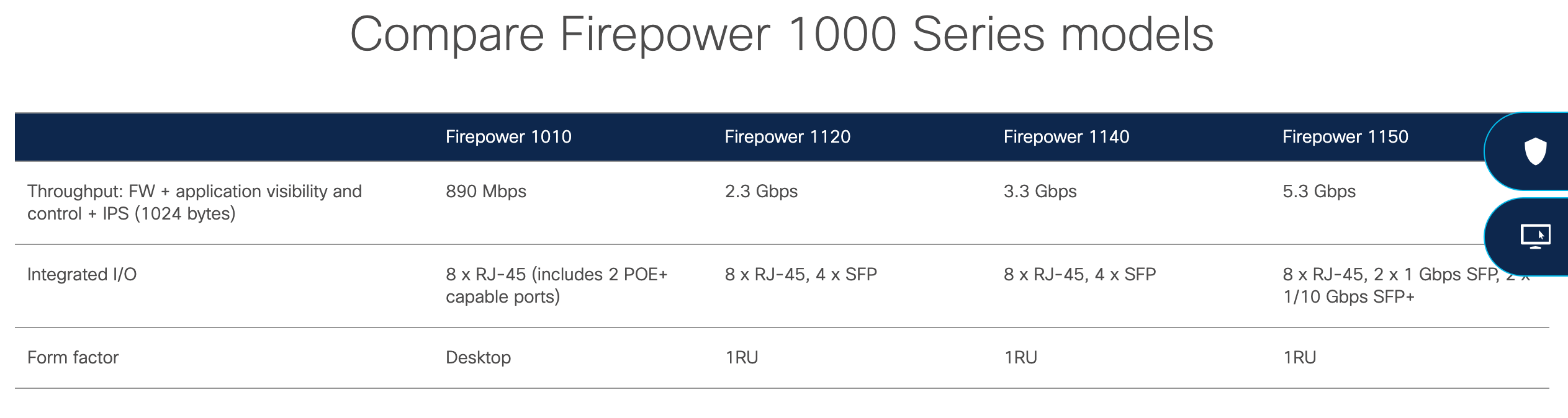
Obviously, the price point on an entry-level Firepower 1010 model will be different than a higher-end 2100 series or 9300 series.
Depending on the provider and organization size, a network firewall can cost anywhere from $300 to $2,000. At the enterprise level, these can range from $20,000 to $200,000+ and higher.
Pricing for WAFs varies as well. These are typically billed based on usage, requests, per user, per application, or per site. Again, it all depends on the vendor.
For a solo user that just wants a WAF to protect a website, it could cost you as little as $20 per month. For an enterprise that needs a WAF to secure a hybrid network, it could be tens of thousands of dollars.
The point I’m trying to make is this—you shouldn’t be looking at the price to determine if you’re going to get a WAF or network firewall. Price should not be the deciding factor.
Getting the best deal requires some shopping around and comparing vendors. But you shouldn’t avoid one over the other because of the price tag. Securing your network and applications must be a top priority, and you can definitely find solutions that fit within your budget.
Now let’s take a closer look at the different features of WAFs and network firewalls to see which one has the advantage over the other in those specific categories.
Attack Defense
Winner = Tie
WAFs and network firewalls both have strengths and weaknesses when it comes to stopping attacks on your network. WAFs alone cannot prevent every attack, and network firewalls alone can’t either.
Web application firewalls have the edge in stopping SQL injections, broken authentications, cross-site scripting (XSS), and L7 DDoS attacks. Network firewalls have the edge for stopping DDoS attacks at the network level, man-in-the-middle attacks, privileged escalations, and unauthorized network access.
You can rely on network firewalls to defend users, organizational assets, and servers. WAFs primarily defend against HTTP and HTTPS servers and applications within the internet-facing zones of a network firewall.
This all has to do with each firewall’s OSI layer coverage. WAFs cover Layer 7, closer to the application. Network firewalls cover Layers 3-4, closer to the network.
When combined, these two types of firewalls fill the weak points of the other—providing a higher level of security for your organization.
Access Control
Winner = Network Firewall
Network firewalls are always better for access control capabilities. You likely won’t find a WAF that offers the ability to restrict permissions or access to a network. In fact, the majority of web application firewalls don’t offer any type of access control options (which is another reason why you need both firewall types).
But access control is a standard offering for network firewalls.
These access control settings are usually highly customizable to accommodate the needs of an organization or IT administrator. You can set these access controls to deny access to specific sites, networks, folders, and more—only granting access to people with specific permissions or credentials.
Fortinet offers zero-trust network access features with its next-gen firewalls. This is ideal for granting access to network applications for remote users.
As an NGFW, IT admins can take this a step further with granular access controls. You can also set up ongoing verification for the user’s identity, device identity, and user access rights.
Not every network firewall access control will be this advanced. But you should be able to set up access controls on a basic level, regardless of the provider or firewall you choose.
Operating Modes
Winner = WAF
At core levels, WAFs and network firewalls each have two modes of operation.
Web application firewalls can operate in passive mode or active inspection mode. Passive mode is only intended for testing purposes, but active inspection mode continuously scans and protects against application-level threats.
Most standard firewalls have two modes—transparent and routed. Transparent mode bypasses layer 3 and only forwards data on layer 2. Routed mode is the main option that operates on layer 3, allowing the firewall to execute static protocols and routing protocols.
WAFs have the edge here because of the continuous scanning and protection. Whereas network firewalls are a bit more reactive than proactive.
This is another reason why it’s in your best interest to go with an NGFW, as you’ll have a bit more flexibility with the modes and protection levels.
Application Level Protection
Winner = WAF
This one is fairly obvious, but it’s still worth mentioning.
As previously mentioned, network firewalls operate on layer 3 and layer 4 of the OSI model. Due to this configuration, network firewalls don’t pay much attention to what’s happening at the application level. Network firewalls are instead focused on validating addresses, monitoring data packets, and protecting the data transfer between networks.
The primary purpose of a web application firewall is to protect layer 7 of a network, ultimately adding security at the application level. This layer includes servers, software, SaaS, applications, and any third-party interface where a user can directly access the network.
Detection Accuracy
Winner = Network Firewall
Web application firewalls and network firewalls will both have systems for alerting IT security admins about incidents, attacks, and vulnerabilities.
Unfortunately, WAFs are known for having issues with false positives. This is especially true for hybrid environments with complex infrastructures. With remote users accessing all different types of applications from different corners of the world, many WAFs trigger unnecessary threat alerts.
On the one hand, it’s better to be safe than sorry. But on the other hand, this can be a hassle for users and IT admins alike to sort out. In some cases, it can impact the day-to-day operations of a company.
Interestingly enough, WAF providers understand that this is a problem. So they try to upgrade the firewalls to prevent false positives from occurring. Here’s an example from the feature section of Fortinet’s WAF product page.
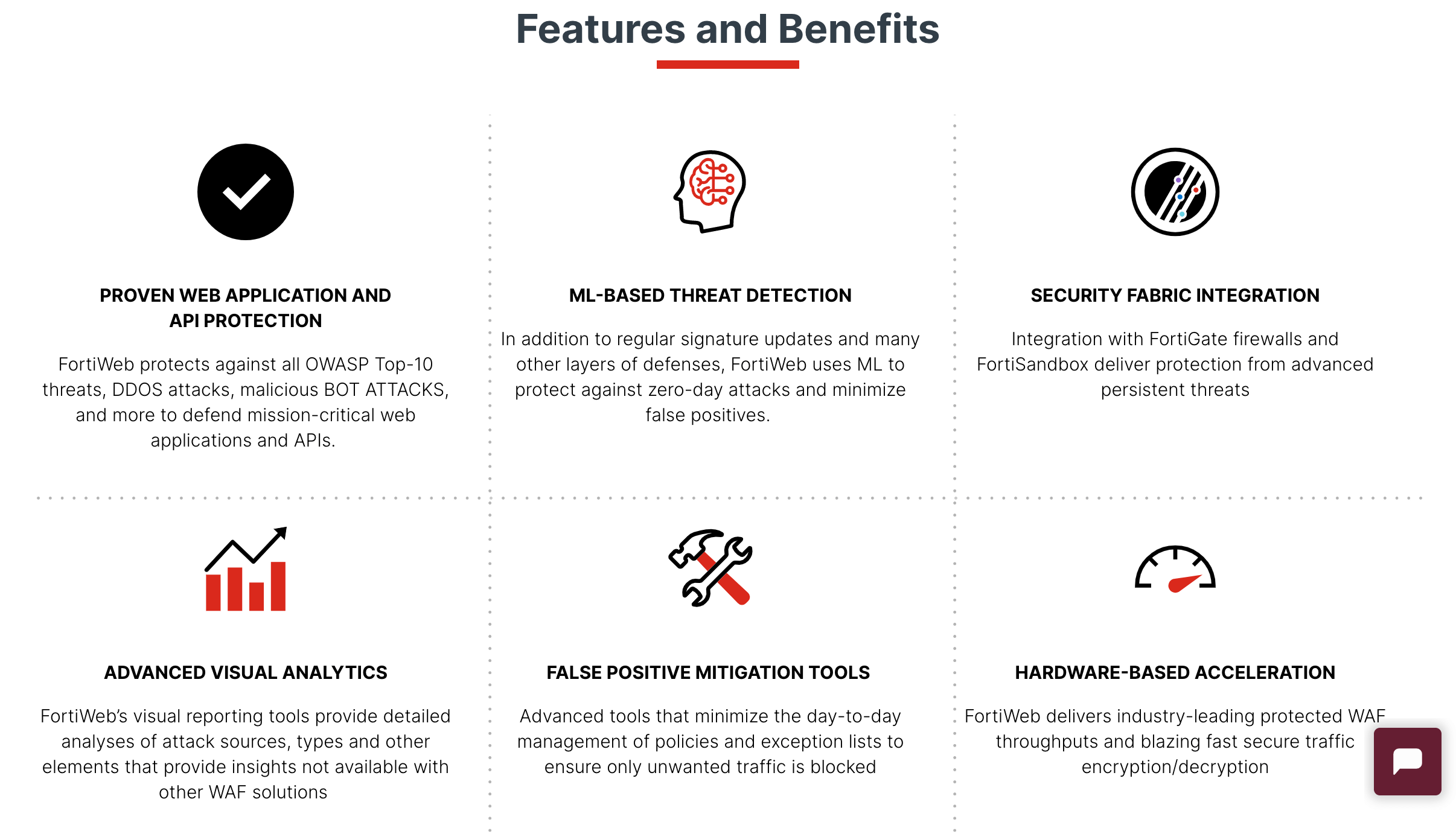
As you can see from the page, Fortinet is clearly trying to show that its technology is forward-thinking with false-positive prevention.
These web application firewalls use machine learning to prevent zero-day attacks and reduce the risk of false positives. The WAFs from Fortinet also come with false-positive mitigation tools.
Your IT admins can set up custom policies to ensure only unauthorized traffic is blocked from the applications. If a false positive occurs, the admin tools will make it easier for you to sort it out quickly.
There’s really no way around this. It’s not like you’re going to avoid getting a WAF altogether because they have more false positives than a network firewall.
Just be aware that this problem occurs more frequently with WAFs, and you should look for solutions like Fortinet that offer workarounds and resolutions.

