Best Network Security Tools
The complexity of network security continues to evolve. As hackers deploy a wider range of tools and attack vectors, you have to find network security tools that can keep up and, better yet, stay ahead.
The best network security tools from years ago may no longer be the ideal option for your network today. Making use of tools that can not only measure network traffic for malicious activity but that can also anticipate the possibility of an attack based on unusual behaviors may provide the best possible protection for your network.
We’ll break down the best network security tools, helping you find the right one for your networking needs.
SolarWinds SEM
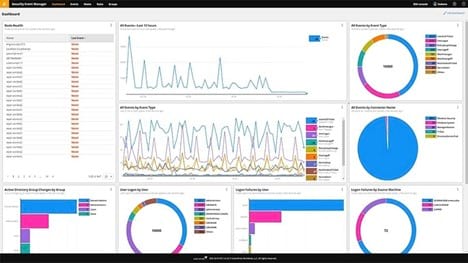
SolarWinds Security Event Manager (SEM) is a strong network security tool that delivers outstanding defense against issues in real-time. It scans the network constantly, comparing any potential issues it finds to its intelligence feed, determining whether the issue represents a true threat.
After it detects any unwanted or potentially dangerous activity on the network, SolarWinds SEM automatically can take action as well. It may suspend a user account that is behaving abnormally. It may block connections with certain IP addresses that are generating anomalies.
To avoid being too aggressive in blocking unusual activity, SolarWinds creates a list of normal network activity as it works. It then compares potential issues to the normal traffic, providing extra data points to try to determine whether the issues represent a threat.
SolarWinds offers software in a wide range of categories, including systems management, database management, and IT security. If you already are a SolarWinds customer, you should be able to easily integrate your other products with your SolarWinds SEM installation.
Pros:
- Offers a well-designed user interface, allowing you to find the information you need quickly
- Integrates nicely with other SolarWinds products
- Automatically implements the most important basic rules that you then can tweak to match your network’s needs
- Provides several filters, so you can drill down to the exact data that you want to see
Cons:
- Software tends to require quite a bit of processing capability
- Self-help documentation resources are not as good as some others
Pricing:
- Subscription license: SolarWinds SEM starts at $2,639 for a subscription license, which has an end date.
- Perpetual license: SolarWinds SEM starts at $5,144 for a perpetual license, which allows the use of the software indefinitely.
The number of nodes involved in sending and collecting log and event information affects pricing and pricing quotes are available. You can also request a free 30-day trial of SolarWinds SEM.
Wireshark
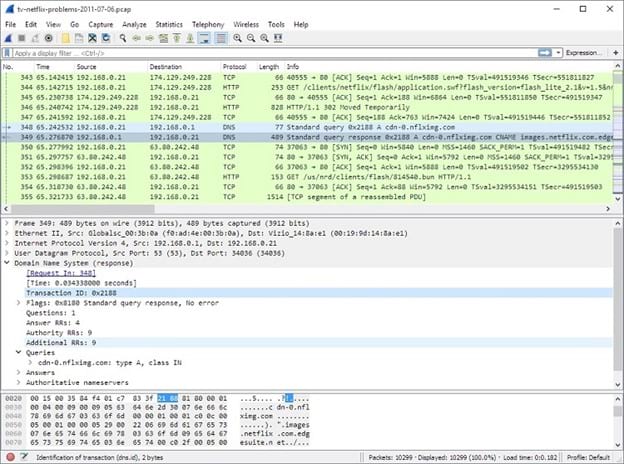
As open-source software, Wireshark easily ranks as a top free network security tool. It delivers impressive features, as well as a wide range of self-help options that give you everything you need to begin deploying the tool successfully.
You’ll receive significant detail regarding the real-time performance of your network with Wireshark. This is Wireshark’s best capability. Few network security tools can match Wireshark’s ability to analyze network data in real-time. It also operates successfully as a packet sniffing tool.
With Wireshark, you will receive as much detail about the different packets as you want to see. It can inspect the bits and bytes that make up individual packets when necessary.
Wireshark is not an ideal choice for you if you do not have much experience with network security. Novices may struggle to use Wireshark successfully.
If you simply don’t trust the idea of using open-source software for network security, you are not alone. Those who deploy Wireshark tend to be extremely loyal to it, though. It is a powerful network security tool.
Pros:
- Simplifies the capturing of traffic on the network for analysis
- Allows for either live analysis of data traffic in real-time or for analysis at a later time of stored data traffic
- Provides the ability to easily spot and analyze software problems on the network
- It’s free to use, yet it remains extremely powerful
Cons:
- User interface is not ideal for novices and could use a refresh
- Doesn’t perform quite as well with encrypted network traffic analysis
Pricing:
Wireshark is free open-source software. However, you can purchase value-added services from third parties, if desired.
Metasploit
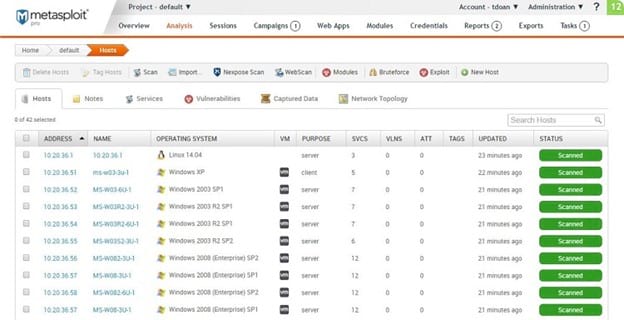
One of the best features of Metasploit from Rapid7 is that its designers approach network security from the perspective of the hacker. You can run simulated attacks just like a hacker might run, giving you unique insights into the network’s security.
Rapid7 offers Metasploit in a free open source version, called Framework, or in a commercial version, called Pro. Metasploit originated as an open-source tool before Rapid7 acquired the code and added the commercial version. For larger networks with significant security demands, the Pro version is the better choice.
With either version, you will receive extensive network security monitoring features. But you also receive advice on managing network security through assessment tools. After running the assessments, Metasploit can provide suggestions for improving your network’s security performance.
Metasploit makes use of a database that delivers constant updating of exploits and vulnerabilities for networks. This ensures your network receives protection against even the newest hacks and exploits.
Pros:
- You can select the version that fits your needs for the network and for your budget
- When operating different network security monitoring projects, you can keep the information completely separate
- Allows for automation of many tests, saving your team quite a bit of time
- Does a good job updating its list of potential exploits, keeping the system up to date
Cons:
- Design of the dashboard could be better
- Can be challenging to export your scanning results to other software
Pricing:
- Free: You can download the free, open-source version of Metasploit Framework.
- Pro: Rapid7 does not publicly release pricing information for Metasploit Pro, but you can request a 14-day free trial period.
Nessus Vulnerability Assessment
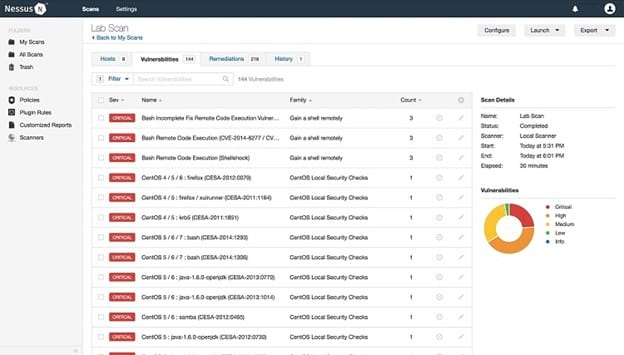
With Nessus Vulnerability Assessment from Tenable, you will receive outstanding scanning capabilities. Nessus monitors hardware, software, and users on the network for any abnormalities. It monitors network traffic constantly, looking for established vulnerabilities as well as the latest vulnerabilities.
Nessus is able to make suggestions about improving network security, including identifying areas that need updated patches or specific attention from your security team.
It even will provide specific lists of any vulnerabilities on the network, explaining the potential ways that hackers could exploit the vulnerabilities. This allows you to focus on the most dangerous vulnerabilities first.
You can select either the scaled-down free version, called Essentials, or the commercial version, called Professional.
Pros:
- Able to scan for vulnerabilities easily and extremely accurately
- Updates itself regularly, so you can catch even the newest vulnerabilities before they have time to hit your network
- User interface is clean and doesn’t contain a lot of clutter
- Reporting functionality offers customizable options and extensive details
Cons:
- Seems to run a little slow when scanning large, busy networks, so breaking up scans into smaller chunks usually works better
- Technical support options are better than some of the other security network tools on our list
Pricing:
- Essentials: Nessus Essentials is a free, scaled-down version of the software. It does not offer content audits or real-time monitoring results.
- Professional: Nessus Professional is available for $2,990 for a one-year license. Two- and three-year licenses are available for slightly lower annual prices.
- Training and support: You can purchase add-on advanced support and on-demand training options for $400 and $195, respectively.
Nessus Professional does have a free seven-day trial period.
Snort
When your network needs an improved ability to detect any potential intrusions on your network, the Snort packet sniffer is among the best network security tools. Its system monitoring tools operate in real-time and provide immediate alerts as to any intrusion detection.
Snort will work with nearly any hardware and operating system combination you may have on your network. Its versatility carries over into the way you can set up and operate it, meaning you can customize its operating parameters to match the specific needs of your network.
Snort is available in both a free open-source version and a subscription-based version. Its origination dates back to 1998, so many network security professionals are familiar with it and trust it.
Pros:
- Excels in detecting potential security issues that simple scans may miss
- Available in either a free or paid subscription to match your requirements
- Open source code means you can verify what’s in the code any time you want
- Flexible design that you can customize easily to match your network’s needs
Cons:
- Pretty complex for novices to deploy and use
- Updates occur regularly, but they aren’t quite as timely as with commercial network security tools
Pricing:
- Community Ruleset: The Community Ruleset version of Snort is available as a free download as open-source software.
- Snort Subscriber Ruleset: Cisco Talos develops and tests the Subscriber Ruleset, offering it for a subscription fee. A one-year Personal subscription costs $29.99. A one-year Business subscription costs $399 per sensor.
Nmap
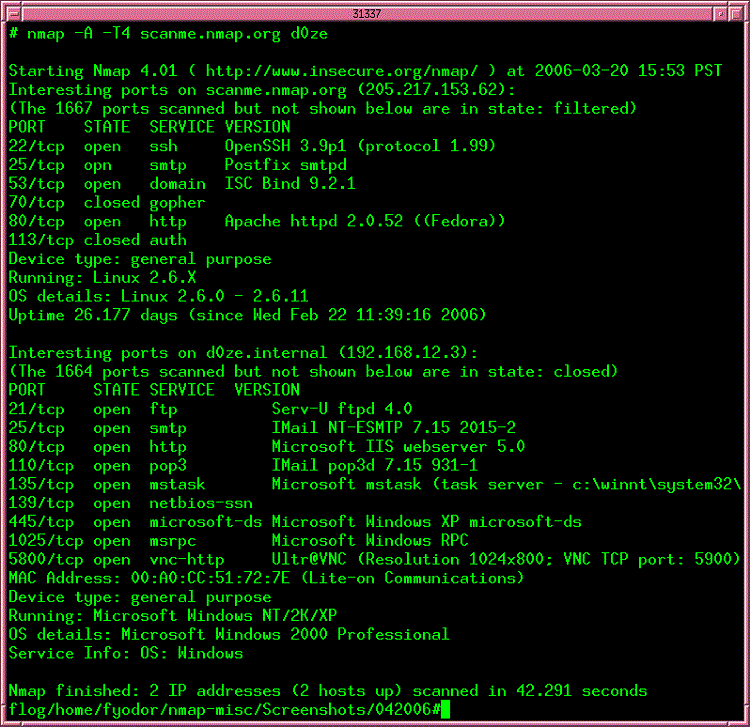
Nmap is one of the most trusted and longest-operating network security tools available. As open-source software, the majority of security professionals will try Nmap early in their careers while seeking to learn more about security deployment techniques and about how to discover vulnerabilities.
For those with experience in security testing and in administering network security tools, Nmap has a clean design that’s easy to use. You won’t have to worry about becoming bogged down or lost in extra features that don’t really help you complete your task.
However, if you do not have experience with network monitoring, the bare-bones interface may work against you. Nmap (short for Network Mapper) works far better for you if you have experience with operating security tools for networking.
Nmap provides raw data about exactly what is happening with your network’s ports. You then will need to interpret that data to figure out the severity of any vulnerabilities. Other tools on our list provide advice on the severity of vulnerabilities and how you should fix them. Nmap leaves this up to you, which some experienced security professionals prefer.
Pros:
- Versatile network security tool, as you can determine exactly what Nmap should check for and how it should run its scans
- Offers operation as a command-line utility or with a graphical interface (called Zenmap)
- Excels at scanning for any open ports that may be vulnerable
- Has multiple community support options that are helpful for troubleshooting
Cons:
- If you choose to run Zenmap, you’ll notice that the interface seems extremely dated
- This product isn’t really the best option for novices
Pricing:
- Nmap is available as a free download for end-users as an open-source software package.
- If you want to redistribute Nmap with proprietary products, Nmap will sell OEM licenses with varying price points, depending on the usage plans and on the size of the company.
How to Pick Your Best Network Security Tool
Step 1: Identify Your Most Vulnerable Areas
To start your assessment of your needs for network security, spend some time studying your network and determining your greatest areas of need.
Some networks need to monitor network traffic in real-time to find suspicious or unusual activity. In this case, a network security tool that excels in intrusion detection, such as Snort, may be your best option. Wireshark also performs real-time analysis that delivers strong results.
Your network may need to simply monitor and study the network traffic, learning what kinds of items involve normal behavior. Over time, the network security tool can use AI and machine learning to determine normal usage, making it easier to detect abnormalities. SolarWinds SEM excels in this area. If desired, it will even automatically block user accounts that exhibit abnormal behavior.
You may struggle with spotting potential vulnerabilities in your network. You may have blind spots that hackers could exploit. If so, uncovering vulnerabilities is an important security feature, as you can’t fix vulnerabilities if you don’t know about them. Metasploit is able to run simulated attacks that help you view your network as a hacker may view it.
Perhaps you need a network security tool that balances all of these areas, rather than emphasizing any of them. Nessus is a strong all-around monitoring tool for all kinds of hardware and software.
Step 2: Determine Whether You Want Automation Or Advice
Some network security tools attempt to reduce the amount of time you must spend monitoring by automating some processes. If you do not have a lot of experience with these tools or if your network security team is already overworked, having automation of certain features is helpful. SolarWinds SEM can automate multiple tasks, including blocking IP addresses involved in suspicious activity.
Another time-saving option involves having the tool provide advice on how to proceed, based on the data it measures. As Nessus monitors the security on your network, it will make suggestions on improvements you can deploy to create a higher level of security.
If you would prefer to study the raw data on your own, removing any potential bias from the network security tool, Nmap is a great choice. Even though manually handling Nmap’s data on your own can take more time, it may be the best option for your network security.
Step 3: Select Open-Source or Commercial Options
After narrowing your list of the best network security tools to those that specifically fit your network’s needs, your final choice should involve picking an open-source or commercial product.
Open-source software is free, which is helpful for some organizations. You also have the ability to view the actual code that makes up the open-source network security tool, meaning you can trust it fully. Wireshark is a very strong open-source option for network security.
Commercial network security tools offer dedicated customer support and technical support options with your pay subscription package. They also typically offer graphical interfaces that can be easier to operate than text-based interfaces that use a command prompt. SolarWinds SEM is a strong commercial network security tool, and it has a free trial period available.
If you may want to start with a free open source option and later migrate to a commercial option as your organization grows, Metasploit has both commercial and open-source options available.

