Best IAM Tools of 2022
Data security is a top priority for every organization. To protect your company’s digital assets, you need a way to control access to various resources.
Identity and access management (IAM) tools make it easy for IT admins to manage user identities and access privileges. IAM software protects network resources by keeping unauthorized users out of the network. These applications also ensure that authorized users can only access systems required to perform their specific duties.
The best IAM tools let IT administrators enforce user access rights based on company policies and user permissions. But not every IAM application is the same. To find the best one for your organization, read our in-depth reviews and buyer’s guide below.
Oracle Identity and Access Management (IAM) Products – Best for Customized IAM Options
Oracle has several different IAM tools to accommodate the varying needs of different organizations. These tools ensure secure access to enterprise apps, accommodating both on-site and cloud deployments.
Whether you’re seeking a solution for IDaaS (Identity as a service) or an integrated identity service for managing cloud infrastructure access, Oracle has you covered.
Oracle actually has four different IAM solutions for you to choose from. Here’s a quick overview of each one, including some highlights and benefits:
Oracle Cloud Infrastructure Identity and Access Management
- Cloud-native IDaaS system
- Supports multi-cloud and on-site environments
- Integrates identity management directly with custom apps using open APIs
- Identifies risk using risk-aware business logic and context
- On-demand scaling
- Unified identity with SSO
- Advanced adaptive authentication service
Oracle Access Management
- Seamless single sign-on to any app from any device
- Full lifecycle management
- Proactive fraud prevention and risk-based authentication
- Integrates with native, custom, and third-party apps
- Integrates with servers, CMS platforms, and data persistence frameworks
- Supports industry-specific authorization standards
Oracle Identity Governance
- Integrated role provisioning
- Integrated user provisioning
- Closed-loop remediation with built-in identity administration
- 360-degree view of user access controls with dashboards and reports
- Role lifecycle management
- Employee self-service tools to manage access
Oracle Directory Services
- Supports cloud, mobile, and social environments
- Unifies storage, synchronization, and virtualization with a directory solution
- Multi-platform support
- Allows for a standards-based solution to support a wide range of hardware and OS
The biggest downside of these products is that there isn’t really an all-in-one solution for everything. So depending on your needs, you might need to use multiple Oracle IAM products to achieve your goals. Fortunately, all of these tools play nice with each other across the Oracle cloud infrastructure.
It’s also worth noting that these are all intended for enterprise use. Small or midsize organizations should look elsewhere.
You can get started with an Oracle Cloud free tier and test the IAM products out. Then you can connect with an Oracle sales rep to discuss upgrades to a paid account and get more information on pricing.
IBM Security Verify SaaS – Best for Differentiating Customer and Employee IAM
IBM Security Verify SaaS is a robust and straightforward solution for identity and access management.
The software comes in two different versions—workforce and consumer. So whether you need an IDaaS for your staff, one for your customers, or both, IBM has you covered.
Some of the tool’s top features include:
- Single sign-on
- Adaptive access
- Advanced authentication
- Lifecycle management
- Identity analytics
- Consent management
You can even use the advanced features to eliminate passwords during the authentication process. Compared to other IAM tools in this category, IBM stands out for its simplicity. But don’t mistake this for a lack of security and power.
I love the fact that there’s a separate solution for consumer IAM. As you probably know, managing access for your customers is very different than managing access in-house.
The consumer tool lets you facilitate frictionless registrations with full transparency. This is a trustworthy way to offer personalized customer experiences while keeping everyone safe.
With IBM, you pay for only what you use. Here’s an example cost for 5,000 users:
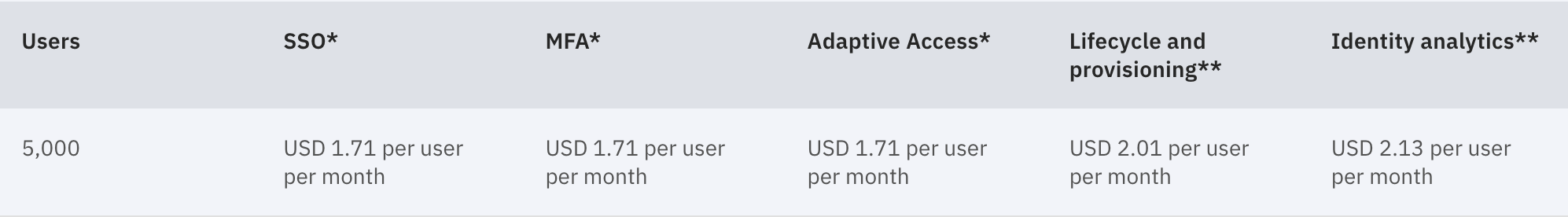
You can always add or remove users on-demand. Resource units are calculated dynamically based on your workforce users, consumer users, and use cases.
IBM Security Verify SaaS is built for larger organizations. Smaller companies might find the pricing structure a bit too expensive.
SolarWinds Access Rights Manager – Best for Auditing and Compliance
SolarWinds Access Rights Manager makes it easy to manage access rights across your entire IT infrastructure. The tool is also great for conducting access audits to ensure your permissions are as secure as possible.
The software also stands out for its support with compliance requirements, like HIPAA, PCI, GDPR, and other mandates. You’ll benefit from comprehensive monitoring for users who can access your company’s most sensitive data.
Again, the audit controls offered by this SolarWind tool really stand out from the crowd. You can use the software to identify high-risk access users and reduce the impact of potential insider threats.
You can easily delegate access rights management and see who has access to what at-a-glance.
Other top features include:
- Active directory provisioning
- Automated SharePoint provisioning
- Automated user account management
- RBAC (role-based access control)
The software starts at $1,838, and you can try it free for 30 days. SolarWinds has subscription options and perpetual licenses available as well.
While the audit reports are great, it still requires human analysis to make decisions. So if your IT security staff doesn’t understand the audits, it could be challenging for them to fix potential vulnerabilities, especially at scale. This is really the only drawback of the software.
PingOne for Workforce – Best IAM User Experience
PingIdentity is another industry leader in the IAM software space. So it should come as no surprise to see PingOne for Workforce rank so high on our list.
The tool is designed specifically for employee access management controls. But what makes it unique compared to other solutions in this space is the user experience.
From IT security admins all the way down to employees going through authorization, PingOne makes things easy for everyone.
PingOne offers a central source of truth as an authentication authority. It works with any cloud, any application, and any directory. So regardless of what your employees are trying to do or where they’re trying to do it from, PingOne can facilitate access controls.
Even if you have a complex IT environment, PingOne can accommodate your needs. That’s why the tool is trusted by more than half of the Fortune 100.
PingOne for Workforce comes with features like:
- SSO
- Passwordless sign-in
- Identity intelligence
- Unified administrator portals
- Authentication and authorization capabilities
PingOne is not an all-in-one solution. So if you need tools for storing user profile information, data governance, API security, and more, you’d need to use other PingIdentity tools.
You can try PingOne for Workforce free for 30 days—no credit card required. Pricing can be discussed after your trial. But like most PingIdentity products, you’ll be charged per user.
OneLogin by One Identity – Best for Centralizing IAM Functions in One Tool
OneLogin by One Identity is a simple way to centralize IAM across all of your apps, devices, and user directories.
You can use it to make sure your staff accesses applications securely. The tool also helps you eliminate passwords while ensuring your most sensitive data stays protected.
The software is great for user management. The provisioning tools make it easy to onboard, offboard, and provision your staff, contractors, and partners from a centralized cloud directory.
OneLogin solves common problems like weak passwords, compliance verification, de-provisioning delays, and password resets.
It comes with features and benefits like:
- Single-sign on with one-click access to all apps
- Secure multi-factor authentication
- Supports biometrics, pins, personal security questions, and more
- Identity and lifecycle management tools
- Centralized reporting and audit trail
- Single source of truth from a cloud directory
OneLogin is also developer-friendly, meaning it’s easy to scale and extend based on your personal needs. The OneLogin API uses restful principles, and it’s secured by OAuth 2.0. So you can integrate custom applications and third-party apps to fit your workflow.
Some users report that the event logs sometimes miss certain actions. But those actions should still be accessible from audit reports.
You can try OneLogin for free with a 30-day trial. Contact the OneLogin sales team to request a quote.
How to Pick Your IAM Tool
There are lots of great IAM tools out there. Even if you’re only considering the top five picks listed above, it can still be difficult to find the right one for you and your business.
Follow the step-by-step buying process below to narrow your options. These steps will help you weed out the bad choices and land on the perfect IAM solution for your organization.
Step 1 – Determine your primary use case for identity access management
With so many features and possibilities in this category, it’s easy to get distracted by all the bells and whistles provided by various tools. Extra benefits are great, but you need to assess the core functions of the software to ensure it addresses your primary pain points.
For example, here are some common reasons why organizations seek an IAM solution:
- Too many user privileges
- No way to track or monitor which employees have access to what
- User authentication issues (like password-only security)
- Challenges addressing security with third-party applications
- Too much friction in the user authentication process
- Poor user experience for customer authentication
These are just a handful of scenarios you might be encountering. But each situation could steer you towards a different tool.
Let’s say you just want to eliminate passwords and use other authentication methods. OneLogin by One Identity is a simple solution.
Or maybe you want an identity access management solution for your customers as end-users. IBM Security Verify SaaS has a consumer-specific product to accommodate your needs.
Start with your primary goal, and ensure the software addresses that pain point. If the software addresses that pain point, but only as a supplementary feature, you can keep shopping around.
Step 2 – Compare cloud, on-premises, and hybrid deployments
Most IT infrastructures will benefit from a cloud IAM solution. Others need a solution that supports hybrid environments, with access management for cloud apps on-site assets.
It’s actually somewhat rare to see businesses that need an IAM tool that’s strictly on-premises. But there are still solutions out there that can handle it.
Oracle has a variety of IAM products that support on-premises deployments, as well as multi-cloud environments. PingOne is another great option for complex IT environments.
Step 3 – Evaluate your compliance requirements
Many organizations face stricter data security standards than others. It’s not just about protecting sensitive company information; it’s about staying compliant with laws and industry standards.
For example, if your company stores sensitive credit card information, you need to ensure your IAM system can handle PCI standards. Or if you’re storing consumer information for people in the EU, you’ll need a GDPR-compliant tool. For companies in the healthcare space, you want to make sure all access control policies are HIPAA-compliant.
If you fall into any of these categories, SolarWinds Access Rights Manager will likely be the best option for your organization. Oracle Access Management also supports industry-specific standards.
Step 4 – Let your IT admins test your top considerations
By now, you should have a shortlist of two or three tools. Comparing feature lists and demos aren’t always enough to establish a clear winner at this point.
Fortunately, most IAM tools let you get started for free. You can usually sign up for a 30-day or 90-day trial.
Take advantage of this trial period.
There’s no reason to rush into a solution. Deployments take time. The last thing you want is to find out two years from now that your solution isn’t scalable, which could have been avoided if you had taken the time to test it out.
Pass the software on to your top IT security officers and let them dive in.
Lots of solutions say they “integrate with anything” or “support users from anywhere.” But you can’t always take this at face value.
Let your IT team test the tools with real employees working remotely or working from different locations. See if it supports third-party tools or custom applications.
Step 5 – Connect with an IAM sales rep
Before you finalize the decision, book a call or session with a support rep from the tool you’re considering. In the enterprise software space, there’s plenty of room for negotiations.
These reps can help you identify other needs that aren’t being met with a single tool.
For example, let’s say you signed up for a OneLogin trial. OneLogin is just one tool from One Identity that can help you with identity and access management. After speaking with a rep, they could assist you with add-on features for things like data governance or API security.
Again, that’s why it’s so important to figure out your primary use case first (discussed in step 1). You can always consider these extras later on. If you mention this during a conversation with a sales rep, you could negotiate a good deal on multiple products.

