Google’s Security Investigation Tool: Top 9 Use Cases for Drive
With 82% of breaches involving data stored in the cloud, IT, Compliance, and Security professionals need every tool available to help with investigations in tools like Google Workspace.
Enter Google’s Security Investigation Tool (GSIT). In 2018, the tool was introduced to help administrators and security analysts identify, triage, and remediate security threats. It’s a powerful solution for investigations as teams address risks in their organizations.
The GSIT can be used with a variety of Google services; it can analyze Gmail log data, identify malicious emails, and manage file-sharing incidents—all within the Google Admin panel. In this post, we’ll explore its nine primary use cases when it comes to Google Drive log events.
Top 9 Use Cases for Drive Log Events
1. Reviewing external access
Knowing which outside parties have access to sensitive company data is crucial to keeping documents secure. For example, many companies do not realize how much access is being granted to collaborators, especially those outside the organization. According to a Google report, the average number of collaborators per Google document is around 13. And, these collaborators are often given more power and permissions than they need.
Let’s say an employee wants to quickly share a Google document with a contract worker, and they add them to the file as an “Editor.” Suddenly that external collaborator has enough permissions to share the document with any account they choose or make the file public for anyone on the internet with the link to see. Public links are a huge issue administrators can investigate with the GSIT. Using the tool’s conditions builder, administrators can set Visibility to “Public on the web” and investigate public access.
Another persistent problem with external access revolves around personal email accounts. Over half (52%) of employees said they or a coworker had accidentally added their personal email account to company documents. And 51% said they’d mistakenly created a document for work using a personal account.
The problem with personal accounts is that access can last for years, without administrators or employees realizing it. Personal email accounts also have fewer protections than corporate accounts, utilizing weak, recycled passwords or lacking strong multi-factor authentication, which leads to greater risks of security incidents.
Companies are also concerned about external parties gaining access to confidential company data. According to our report using Gartner Peer Insights, vendors being given access to company information was the greatest information security threat for the majority of companies surveyed. These fears could be warranted; in a separate survey, we found that 60% of employees never or sometimes remove vendor access once the vendors are no longer working with the company.
2. Offboarding and layoff events
Administrators also utilize the GSIT during offboarding processes. After a layoff event, it’s vital to ensure no one is taking company documents when they leave. We found that 45% of employees admitted they’d taken documents before leaving an employer. And another 9% said they’d rather not say if they had.
Using Google’s investigation tool, administrators can look at various events including if employees downloaded, renamed, copied, opened public links, or added external collaborators (like their personal accounts) to files. These could be indicators that company data is at risk of leaving the organization and needs to be investigated further.
Over half (57%) of tech leaders said when an employee isn’t properly offboarded, the risk of a cybersecurity attack through an unmanaged account terrifies them the most, according to a Gartner poll. Administrators can use the GSIT to help with proper offboarding protocols so they can reduce the risk of data exfiltration or unmanaged accounts having access to company files.
3. Security incidents and data breaches
For some organizations, the urgent need to investigate issues in Google Drive comes after a security incident or data breach has already happened. This process can last longer than expected. According to IBM, it takes an average of 277 days to identify and contain a data breach. A security incident may not be a one-time event; 83% of the organizations IBM studied in 2022 had multiple data breaches.
Administrators can use the GSIT to investigate what happened during the breach and better understand what precautions should be taken in the future. They can also utilize the log data to understand exactly what information was accessed as part of the breach, and what actions were taken by compromised accounts.
4. Compliance and contractual concerns
Another key use case for the GSIT is ensuring sensitive information is not being modified due to compliance or contractual obligations. For example, the Sarbanes Oxley Act (SOX) states that any important documents related to auditing and reviewing financial statements must be kept for seven years after an audit or review is done. Should any revisions occur to financial reports, companies must note what was changed, by whom, when, and why—for records retention policies.
Companies may also need to make sure important client information isn’t being modified due to contractual purposes. They may monitor whether or not client data is being modified due to the nature of their work. Or, companies may have contracts with their customers or as part of GDPR compliance related to safeguarding information and making sure it’s properly deleted. It helps to investigate these issues with the GSIT, ensuring that companies are staying compliant and within their contracts with customers or following regulations like GDPR.
5. Investigating abnormal behavior
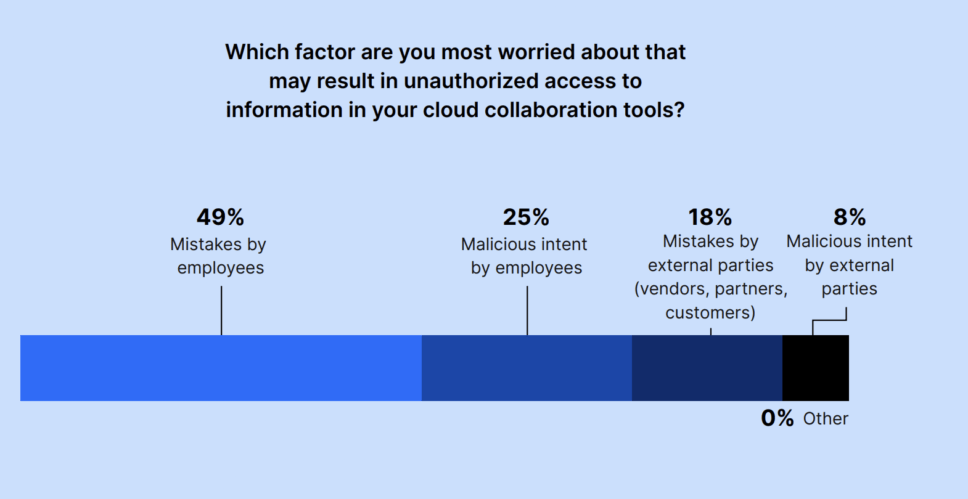
Sometimes, administrators need to investigate a user’s activity throughout a specific period. This could be due to common, everyday errors. For example, 49% of IT and Security leaders were worried about mistakes by employees when it came to unauthorized access to data in cloud collaboration tools. Administrators also may want to reduce the risk of insider threats; 25% of leaders were concerned about malicious intent by employees resulting in unauthorized access to data in cloud collaboration tools. Although rare, this can happen, and the GSIT allows administrators to investigate specific users using its condition builder. For example, admins can search attributes including “Actor” and “Date” to figure out if anything went amiss.
6. Legal investigations
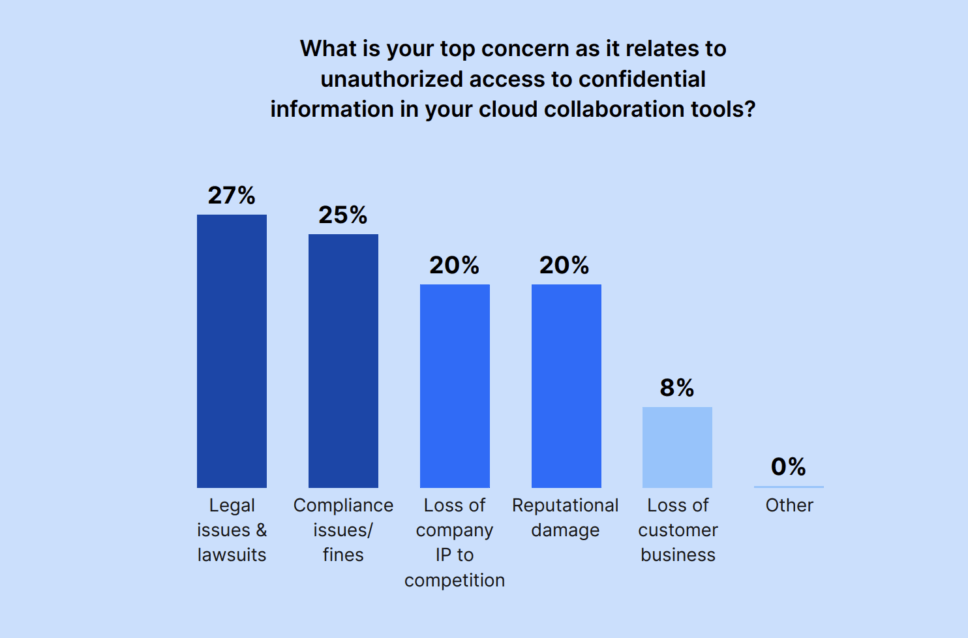
Legal issues and lawsuits were the top concern for IT and Security leaders when it came to unauthorized access to confidential data in cloud collaboration tools. Using the GSIT, administrators can dig into issues for legal purposes and eDiscovery investigations. During an eDiscovery investigation, different data types may be analyzed and reviewed for litigation purposes. This includes confidential files or email messages. Using the GSIT, administrators can view sensitive message content or investigate a specific user.
7. Searching shared drives
Although shared drives have only been around since 2017 or so, they come with a large amount of risk. A company’s shared drives could contain confidential information, without everyone in those shared drives realizing it. Sensitive customer data might be stored in a different shared drive (or sub-folder within a shared drive) for every customer, and someone who should not have access could gain unnecessary permissions through a sharing misconfiguration. Administrators often need to monitor collaborator access permissions for these shared drives or see if any sub-folders have Public or Company links. Being able to search and investigate shared drives is vital for keeping data safe.
8. Looking into labels
Labels are a newer feature in Google Workspace that can be used to aid security processes. For example, documents may have a “Confidential” label, and administrators want to view all the events happening on those files. Or, a file has a label related to a specific customer or project that the administrator needs to check on. Using the GSIT’s condition builder, administrators can search using label titles and label field display names.
9. Remediating issues
The GSIT stands out from Google’s audit and investigation page by allowing administrators to take key actions based on their search results. Using the tool, administrators can quickly remove or add collaborators, change or transfer ownership of files, and restrict downloading or copying of files for a subset of files matching search criteria that had activity over the last 180 days.
Google’s Security Investigation Tool offers a versatile solution for a wide range of use cases. From pinpointing unauthorized access to detecting potential risk, administrators must harness the tool’s capabilities to ensure a more secure environment. For a detailed guide on how to use the tool in your organization, visit here.

